Recently, I collaborated with a number of researchers from the Software Systems Laboratory of Columbia University, on a study regarding POSIX (Portable Operating System Interface) abstractions. In a nutshell, we measured how and to what extent traditional POSIX abstractions are being used in modern operating systems, and whether new abstractions are taking form, dethroning traditional ones. The results of this study were presented at the 11th European Conference on Computer Systems (EuroSys ’16).
In one of our experiments, we examined which POSIX calls are used by both benign Android applications (~1 million) coming from the Google Play Store, and malicious Android applications (1260) taken from a well-known dataset. The popularity of POSIX calls between the benign and malicious applications can be seen in Figure 1. An interesting observation involves outliers illustrating that there are POSIX interfaces which are popular only for malicious applications. Table 1, presents a set of indicative abstractions that are popular among malicious apps and unpopular among benign ones.
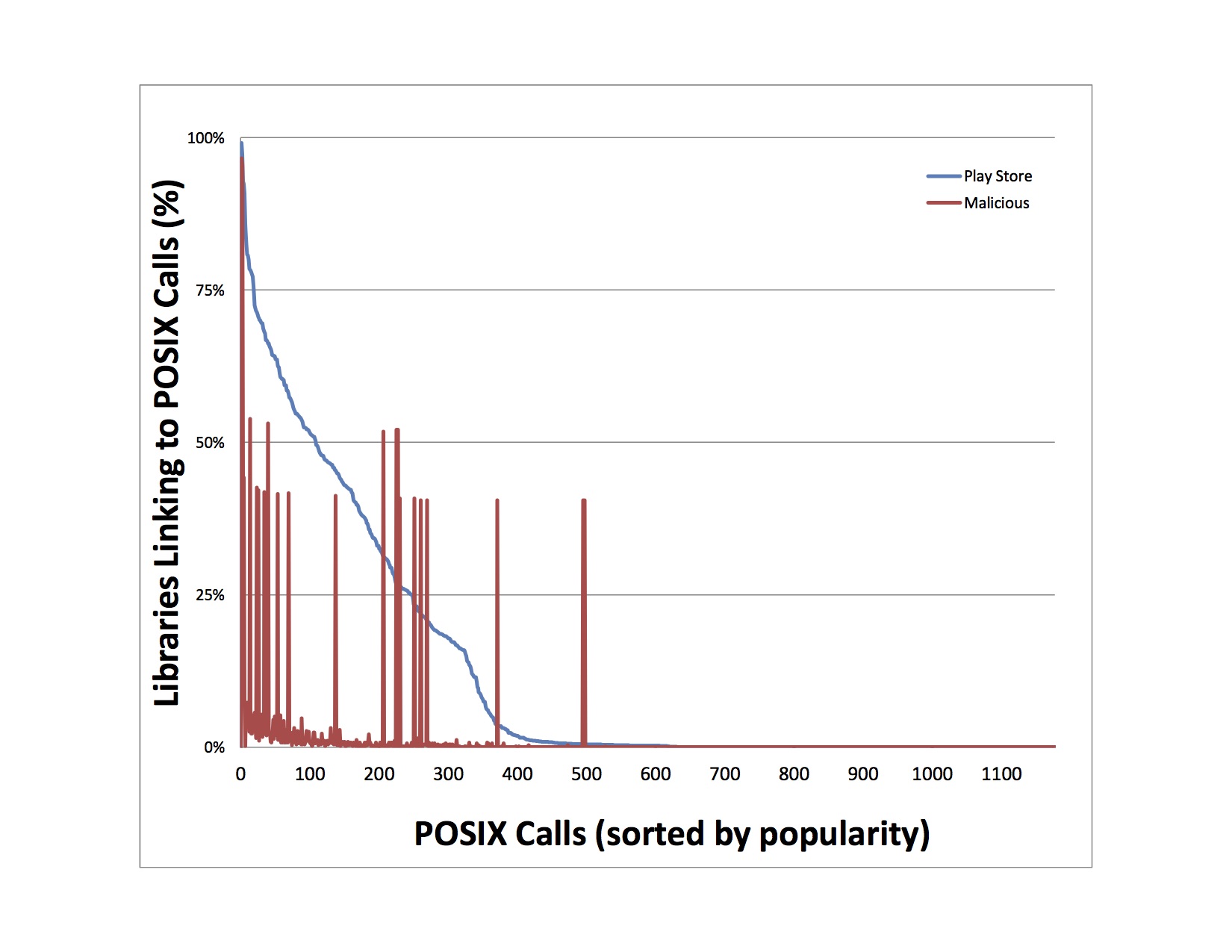
Figure 1: Comparing the popularity of POSIX calls between benign Google Play applications and malicious applications (taken from a popular dataset). There are some outliers identifying POSIX calls, which are popular only for malicious applications.

Table 1: Popular POSIX abstractions among malicious applications (and at the same time unpopular among benign ones).
We attempted to create a simple filter that identifies potentially malicious applications based on the three most unpopular abstractions among benign applications and at the same time popular among malicious ones. In particular, we checked if an application uses at least one of the following abstractions: ptsname, unlockpt (two pseudo-terminal functions – malicious application developers are most likely attempting to exploit interfaces known to be old, poorly maintained, and buggy) and setsid. We checked our filter against a set of applications taken from the Google Play store (465000). Our initial findings though, were not significant. Specifically, our filter indicated that 1633 applications were suspicious. To validate our result, we checked these applications against the 54 antiviruses provided by the VirusTotal service. To achieve this, we used the framework that I presented in my previous blog post. We found that 413 (25.29%) of them are potentially malicious. Furthermore, Figure 2 indicates that in most cases only one antivirus issued an alarm, which is probably a false positive.
In my next post I will discuss about a more robust filter based on binary classifier and also about potentially malicious applications that include obfuscated libraries.

